Trustwave, Telarus Announce Strategic Global Partnership
Trustwave is partnering with Telarus, a leading technology services distributor (TSD), which will ...
Read MoreSign up to receive the latest security news and trends straight to your inbox from Trustwave.

Trustwave is partnering with Telarus, a leading technology services distributor (TSD), which will ...
Read More
Clients often conflate Offensive Security with penetration testing, yet they serve distinct ...
Read More
Editor’s Note – The situation with the Change Healthcare cyberattack is changing frequently. The ...
Read More
The (apparent) takedown of major ransomware players like Blackcat/ALPHV and LockBit and the threat ...
Read More
Companies engage with a managed detection and response (MDR) provider to help ensure they detect ...
Read More
Despite investing in costly security solutions, keeping up with patches, and educating employees ...
Read More
Two of the greatest threats facing technology-focused organizations are their often-quick adoption ...
Read More
New Mexico Governor Michelle Lujan Grisham issued an Executive Order to shore up the state’s ...
Read More
Recent cyberattacks and the Department of Health and Human Services (HHS) Office for Civil Rights ...
Read More
Trustwave SpiderLabs’ recent threat report on the hospitality industry included a reminder that ...
Read More
Among the due diligence a company should perform when signing with a managed detection and response ...
Read More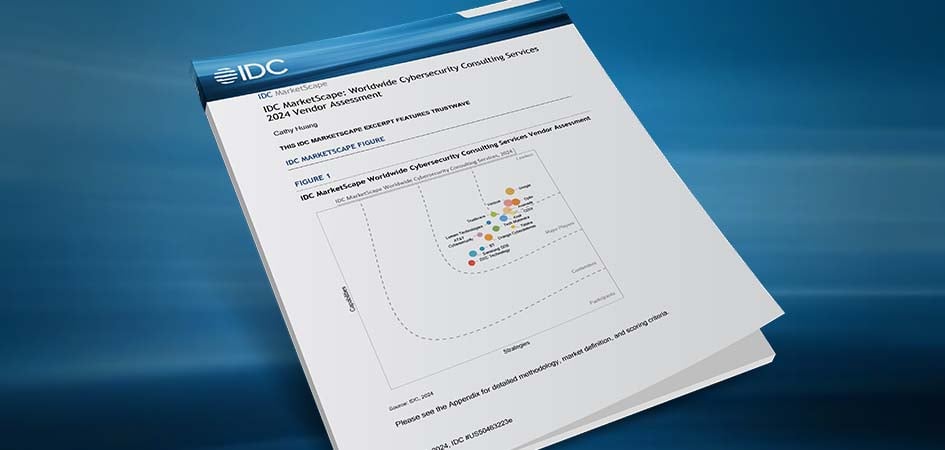
Trustwave was named a Major Player in the IDC MarketScape: Worldwide Cybersecurity Consulting ...
Read More
Trustwave today added Threat Intelligence as a Service (TIaaS) to its offensive security portfolio ...
Read More
Trustwave today announced it will offer clients expert guidance on implementing and fully ...
Read More
Today's ever-shifting threat landscape demands a multi-pronged approach to cybersecurity. ...
Read More
Trustwave MailMarshal will receive a massive upgrade on March 28 that will add four new levels of ...
Read More
Anyone who has visited a casino knows these organizations go to a great deal of expense and ...
Read More
While third-party products and services are crucial to everyday business operations for almost any ...
Read More
Comparably, a leading workplace culture and compensation monitoring employee review platform ...
Read More
Criminals have always been among the first to adopt the latest technology to benefit themselves ...
Read More
Trustwave Government Solutions (TGS) was named as a Major Player in the inaugural IDC MarketScape: ...
Read More
Managed detection and response (MDR) providers often tout how quickly they can onboard new clients, ...
Read More
Trustwave has been named a Representative Vendor in Gartner just released the 2024 Market Guide for ...
Read More
As technology has become available, the hospitality industry has focused on making the most out of ...
Read More
The security analyst firm Frost & Sullivan positioned Trustwave as a leader and top innovator ...
Read More
The integration of Artificial intelligence (AI) is forcing a significant transformation in the ...
Read More
A ransomware attack can demoralize or debilitate organizations quite like no other. Not only does ...
Read More