As the world shifted into remote work and distant learning during the pandemic lockdown, e-commerce accelerated as more consumers turned to online shopping apps and websites. Customers who shop online are familiar with email confirmation for their orders. But what if you receive an email confirmation for something that you never bought? It might be a fake order scam, and they are now being sent through Google Groups.
What is a Fake Order Scam?
In an earlier blog, we described fake order scams as messages that notify victims regarding a product, service purchase status, or confirmation that originally was not placed by the recipient. The scam works by getting the customer to try to cancel the supposed order by clicking a link or calling a telephone number. The end goal of the threat actors is to steal the victim’s personal credentials - name, address, credit, or banking information, or trick the victim into installing malware on their computer.
In October 2022, the Federal Trade Commission (FTC) released an article detailing how to recognize a Geek Squad renewal scam. Scammers impersonate different business establishments such as online shopping platforms, security vendors, and logistics services. Geek Squad, Best Buy’s tech support service for hardware repair and replacement plans, is no exception to this. It is one of the most popular computer help services available. Due to its popularity, this brand is heavily impersonated in different scam operations.
The Suspicious Google Groups Notification
We observed a new variant of the fake order scam and this time, it’s using the Google Groups platform to send malicious messages to people’s inbox.
Google Groups is a service used for communication and collaboration within discussion groups. It provides three features: email lists, discussion boards, and collaborative inboxes.
Shown below is a legitimate email from Google Groups that notifies the recipient that they have been added to a group called ‘Client Support Geek Squad1389kuxi’. Based on the group’s name, it hints that it has something to do with the support service of the famous company.
 Figure 1 Notification received by victims when they are added to a Google Group
Figure 1 Notification received by victims when they are added to a Google Group
Clicking the ‘View this group’ button will lead to the legitimate Google Groups website where members can see and receive messages in the group conversations. However, the group itself is just an imitation of Geek Squad support channel.

Figure 2 View of the Fake Geek Squad Support Group
Inside the group, members can discuss any topic using the Conversations feature. According to Google, groups can contain one or more conversations. A conversation contains one or more posts and members can reply either to everyone or only to the author. Either way, members will receive email notification of the activities in the conversations.
Google Groups works like a forum and an email distribution list. When an owner or members of the group create a new conversation or replies to a post, a notification containing the new post or reply is sent individually to all its members. With this, threat actors can automatically add email addresses, even non-Gmail accounts, into a group and start spamming users. They then create a conversation post with fraudulent content and send it out to the members. This is how the scam messages end up in the victims’ mailboxes.
The Scam Payload
Threat actors curate a variety of email templates that resemble an order confirmation from the Geek Squad and distribute them to all the members of a group.

Figure 3 Google Groups Notification Containing the Fake Order Scam
These emails are complete with customer ID, purchased item and warranty expiration, date of transaction, invoice number and the fake customer support telephone number. It may seem legitimate at first glance, but there are obvious red flags in this email.

Figure 4 Header Details of the Scam Email
The first major red flag is seen in the email header where the sender address is made to look like it came from the official Geek Squad team. Since the email is a Google Group notification, the sender contains the googlegroups.com domain. Authentic emails from Geek Squad are sent using their official customer support email address, not from a Google group.
In the email body, the generic greeting of ‘Dear Valid User’ is questionable as legitimate receipts will have the customer’s name in the message. The formatting of the message also contains inconsistent font sizes and alignments.
Another item to note is the telephone number ‘+1(888) 864-1561', which does not belong to the Geek Squad. This is the scammer’s number that victims are being tricked into calling. According to Geek Squad’s Frequently Asked Questions (FAQ) page, their official hotline is 1-800-433-5778, at the time of writing.
Shown below is another scam email sample notifying the recipient of a recent purchase from the Geek Squad.

Figure 5. Another Example of Fake Geek Squad Order
Based on our collected samples, the indicated price in these fake orders cost hundreds of dollars. This price might be hefty for users, especially if they did not intend to pay for such services. Scammers intend to cause panic to the recipient and trick them into immediately cancelling their orders by calling the listed telephone number.
What happens when you call these phone numbers?
Deceived victims who call the listed phone number often believe they are speaking directly with a legitimate Geek Squad representative about a refund. Typically, scammers assure the victim that the refund can be processed and require filling out an online form first. They then instruct the victims to access a website where an application can be downloaded to remotely access the victim’s machine. Once the scammer has remote access, they pretend to process the refund while secretly browsing their files and accessing sensitive information such as personal documents, banking details, and passwords. They may also install malicious files like spyware programs to steal even more sensitive information.
Some scammers trick the victims into accessing their bank accounts under the guise of verifying the refund, thus capturing their banking credentials. There are other cases where scammers fake a transaction and make it look like they have accidentally over-refunded and ask the victim to return the excess amount. Usually, they request it through irreversible payment methods like gift cards and ask for the gift card number and PIN.
These deceptive schemes not only cause financial harm for victims but also lead to breaches of their personal data.
A Rising Trend of Google Groups' Scam Emails
Trustwave SpiderLabs has identified a notable surge in these Geek Squad scam email activities delivered via Google Groups. These deceptive campaigns, which we've been closely monitoring, began their momentum in late June. Interestingly, the frequency increased substantially from the end of July through August. As of this report, the campaign remains active, with its peak, so far, being observed on August 8, when over 800 samples were detected by Trustwave’s MailMarshal.

Figure 6. Chart showing a two-month daily activity of Geek Squad scams delivered via Google Groups
In relation to this, we also observed an increase in volume of unsolicited Google Group invitations from the end of July with heightened activity persisting through August. There were notable peaks in invitation volume on August 7 and 9, which align with the influx of fake order scams as illustrated in the preceding chart.

Figure 7. Chart showing a two-month daily activity of Fake Geek Squad Google Groups Invitations
How Scammers Utilize Google Groups for Order Frauds in this New Scheme
The creation and use of Google Groups for spamming is fairly easy and requires only a few steps.
i. Creation of Deceptive Google Groups

Figure 8 The image provided above outlines the simple steps in creating a Google Group.
Scammers start off with setting up each group for their fraudulent intentions:
a. Use of Familiar Branding:
Scammers create groups that are named to resemble and pretend to be a well-known brand like the Geek Squad. These group names and addresses contain either the brand name, ‘support center’, ‘customer care’, ‘help desk’ and other variations. Here are the other examples of the ‘from address’ used in this campaign.
Support-center4190wlrv-noreply@googlegroups[.]com
helping-society-1500-noreply@googlegroups[.]com
helping-group5466565ggdf-noreply@googlegroups[.]com
team-geek-squad3849dgqv-noreply@googlegroups[.]com
customer-careteam45645fg@googlegroups[.]com

Figure 9 Description of a Fake Geek Squad Google Group
Here is a description from one of the fake groups that contains a welcome message and short introduction for the members to make it appear legitimate.
b. Volume of created groups:
Scammers strategically create large numbers of groups as it allows them to send scam messages from multiple different addresses. It also helps maintain their operations whenever a group or a sender address gets blocked by Google or spam filters.
The image below shows numerous suspicious groups we found within Google Groups posing as Geek Squad Support Teams. Our search revealed the existence of over 2,000 fake support groups. As seen in the activity level, these groups post about 1 to 5 messages per day, and some are more active than others.
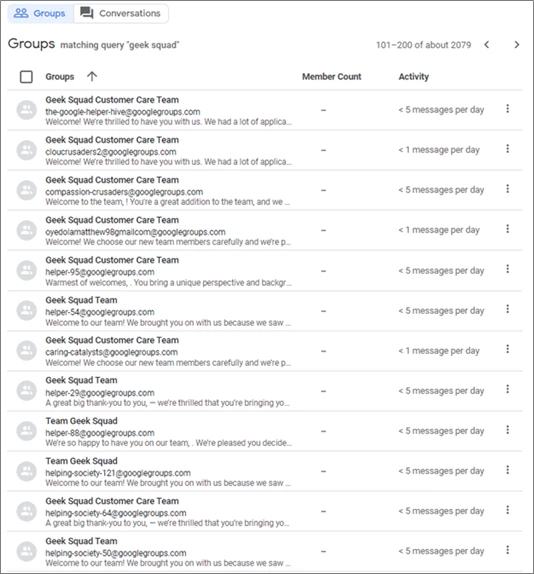
Figure 10 Query of Google Groups Relating to Geek Squad showing around 2000 search results.
As shown in the images below, we’ve seen that each group comprises about 300 members. Considering that there’s more than 2,000 groups involved in this scam campaign, we can assume that there’s an estimated 600,000 targeted users.

Figure 11. Number of Members Per Google Group
ii. Victim Invitations
Scammers can invite users either during the group creation process or after the group is already set up. Owners of the group can toggle on the ‘Directly Add Members’ setting (as seen on Figure 12) in the creation process to automatically add users in a group without needing to ask permission or accept invitation. Subsequently, individuals added to these groups are now part of the scammer’s mailing list where any message or conversation posted in the group will be sent to all the group members.

Figure 12 This image shows the third stage in the group creation process, where there is an option to add members directly to the group.

Figure 13 Google Groups Invitation Email Subject Lines
As mentioned earlier, these groups mimic Geek Squad’s customer support. The notifications that victims receive when they are added to the group contain email subjects similar to those listed above.
Non-Gmail accounts can also be added in these groups, and they don’t even need to access the actual group website to receive notification and conversation emails.
iii. Email Spamming via Conversation posts
Using the platform’s mailing list feature, threat actors can broadcast or send out multiple malicious conversation posts to its members.
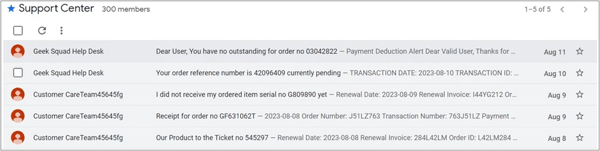
Figure 14 Google Group with Multiple Fake Order Scam Conversations
One interesting detail about these conversations is that each post has a different fraudulent hotline. All the observed malicious posts use the US country calling code of +1. This could indicate there’s a larger operation or a call center driving this scam campaign with a primary focus on targeting American residents.
Conclusion:
Threat actors continue to evolve their spam tactics by utilizing Google Groups to send scam messages to numerous users. By exploiting legitimate platforms such as Google Groups, there is a higher chance of delivering spam to victims. Messages sent through Google may occasionally evade traditional spam filters due to its trusted reputation. On top of this, this campaign impersonates Geek Squad, a well-known customer support service. By combining these elements, fraudsters create seemingly legitimate malicious emails.
Keeping up to date with the latest spam and social engineering techniques is important to prevent the general public from being victimized by scam campaigns. As always, we remind everyone to stay vigilant in this ever-changing digital landscape.













